In the wake of two well publicized zero-day exploits
sending out a fake e-mail from Microsoft urging recipients to click on the links to patch their systems.
The message, which says it’s a Windows Live critical update from Microsoft (NASDAQ: MSFT), bears the Windows logo and has several links purportedly to the software giant.
One urges recipients to click on it to install updates, another to download Microsoft Update to scan their computers, and yet another purportedly lets recipients read Microsoft security bulletins.
The attack, discovered by security product vendor Sophos and mentioned on its senior technology consultant Graham Cluley’s blog today, also has links to terms of use, trademarks and a privacy statement.
The links point to an executable program hosted on a Web site in Italy, Cluley said in his blog.
“Microsoft is aware of reports of malware launching from fake e-mails with malicious links posing to be a download for the most recent security updates from Microsoft,” Christopher Budd, the vendor’s security response communications lead, told InternetNews.com by e-mail.
“Users should exercise caution with requests received from unknown sources, or received unexpectedly from known sources.”
Budd also noted Microsoft updates are only available through Windows Update and Microsoft’s malware removal site.
Patching can be dangerous
Microsoft last issued two out of band patches, meaning patches outside its regular monthly cycle, for new zero-day exploits in December.
Today’s attack could be an attempt by spammers to capitalize on that fact in the hope users think a new out of band patch has been created, Paul Ferguson, advanced threat researcher at antivirus vendor Trend Micro, told InternetNews.com.
Microsoft doesn’t e-mail people about updates,” he said. “They try not to issue patches out of their normal monthly patch cycle unless it’s a critical issue, and even then they don’t send out e-mails.”
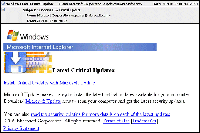 Click on the graphic for a larger view. Source: Sophos |
Randy Abrams, director of technical education at antivirus vendor ESET, told InternetNews.com that fake update e-mails from Microsoft are an old form of attack. They were successful because, at that time, vendors advised users to open only e-mails from trustworthy sources.
“No one explained what trustworthy sources are, so we had a problem,”
Abrams said. “Eventually, Microsoft advised users not to open attachments at all.”
Abrams went so far as to advise users not to open any attachments or links, even from a trustworthy source. “Go to the source’s Website and key in the URL by hand,” he advised.
Users who want to open links can do so if they are running Sandboxie, an application that runs programs in a sandbox, which is an isolated space on a user’s hard drive, Abrams said. Available at this Web site, Sandboxie prevents programs from impacting other applications and data on the user’s hard drive.
“It will sandbox Internet Explorer, Google Chrome, Mozilla, Windows Media Player, and it’s an awesome line of defense,” Abrams said. “It works really, really well.”


