 Facebook efforts to block phishers. Source: Facebook. Click to enlarge. |
Facebook early today suffered its second phishing attack in 24 hours, but the social networking site took swift action to resolve the matter.
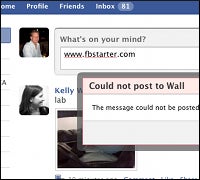
Yesterday, attackers worked to lure Facebook members to FBAction.net, a site displaying a bogus Facebook login page that hijacked users’ accounts. Today, a second attack appeared, this time using fbstarter.com.
While the creator of the site remains uncertain — the site is registered to “Boris Soroka” in Moscow, according to Whois records, which aren’t necessarily legitimate — Facebook and its security partners are moving quickly to lock things down.
“We’ve already blocked www.fbstarter.com from being shared on Facebook, which stops the spread,” Facebook spokesman Barry Schnitt told InternetNews.com. “Now, we’re deleting that URL from walls and inboxes. We’ve also blocked access to the URL so if someone does find it on Facebook [on their wall, in their inbox, or in an e-mail notification] it won’t send them to the destination. Finally, we’ll automatically reset the password on any account that sent the malicious link. Thus, the data becomes useless to the bad guys very quickly.”
He also said that, in addition, Facebook works with security player MarkMonitor to limit the damage.
“We send them URLs and they get them added to the browser blacklists and work to get the sites taken down. They got that site taken down, too. Today’s site has been down most of the morning. MarkMonitor and Facebook are watching it closely, though,” he said.
Yesterday, users were being lured into entering their information at the site FBAction.net. Once users entered their e-mail and passwords, many reported that their password has been switched and all of their friends had been e-mailed from the account.
Fortunately, the social networking site took swift action yesterday as well and the threat was vanquished by the end of the afternoon.
“The initial attack yesterday was down within 52 minutes of the report,” Fred Felman, chief marketing officer for MarkMonitor, told InternetNews.com.
Schnitt also offered the following advice to avoid becoming a victim of phishing scams at Facebook: “They should always, always make sure the address is www.facebook.com and nothing else when they are logging in. Also, they should have unique logins and passwords for the sites they use. One final thing, users should be very suspicious of any message, post or link they find on Facebook that requires them to log in again. That should not happen.”
Meanwhile, MarkMonitor and Facebook today publicly announced their work together — with the social networking site tapping MarkMonitor AntiFraud Solutions to supplement its own in-house security efforts in protecting users against malware attacks.
Facebook, which already uses MarkMonitor AntiFraud Solutions to help combat phishing attacks, also said it is expanding its use of MarkMonitor to further protect the Facebook platform and its millions of loyal users against ongoing malware attacks.
“Our deep commitment to the safety of our users requires a strong proactive security strategy, best-of-breed technology and active engagement with industry leaders,” Ryan McGeehan, threat analyst at Facebook, said in a statement. “MarkMonitor demonstrated that it understood the complexity of the phishing issue we were facing so it was a natural next step for us to bolster our own security systems with their antimalware solution.”
Social networking sites such as Facebook can be prime targets for malware attacks due to the brand’s strong appeal, which can be used to trick users, and the ability to use the communication platform as a distribution channel. Once infected, malware can cause havoc on a user’s computer by deleting important files and creating general disruption to the user experience. Malware can also achieve nefarious purposes by residing silently on a system and capturing personal information such as usernames, passwords and social security numbers that can be used to perpetuate identity theft.
Facebook placed seventh in a list of brands tapped for phishing for the month of March, with 104 phishing Web sites targeting Facebook, according to phishtank.com.


