 |
Apple (NASDAQ: AAPL) has released its Software Update version 2.1 as the company refreshes its new Safari 3.1 browser to fix four vulnerabilities. Two of the issues are specific to Safari running on Windows.
In one of the patched issues, Apple notes in its advisory that a maliciously crafted Web site may control the contents of the address bar. It’s a flaw that could have potentially led to spoofing or unintended user information disclosure.
The second Safari for Windows issue involves a memory-corruption flaw that could be triggered when downloading a file.
“By enticing a user to download a file with a maliciously crafted name, an attacker may cause an unexpected application termination or arbitrary code execution,” Apple stated.
Having updated software to ensure proper security is a must for all technology users. It’s something that has become particularly important for Apple users lately with QuickTime
software being frequently patched.
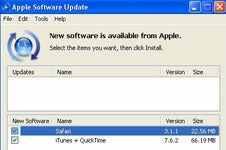
Sometimes it’s also important to not just update software applications but the software updater itself. In Apple’s case the move to update its Apple Software Update technology this time isn’t just about security; it’s also about clarity.
“Apple’s Software Update application is the easiest way for Mac and Windows users to make sure that they have the latest software from Apple,” an Apple spokesperson told InternetNews.com. “In this latest release we have made it easier for customers to identify between software updates and new applications.”
Last month Apple came under attack by Mozilla CEO John Lilly for what Lilly alleged was the unethical practice of including updates for software (in particular the Safari Web browser) that a user had not previously installed.
Prior to update version 2.1, a user would have seen Safari (and other software that had not been installed such as iTunes) listed in the update window.
The move by Apple doesn’t go far enough according to Mozilla staffer Asa Dotzler.
“This is a good first step,” Dotzler wrote on his blog. “Now Apple needs to stop checking the box for New Software by default.”
Users of Safari for Mac and Safari for Windows are both at risk from a pair of flaws in Apple’s WebKit rendering engine. Apple has reported an issue in how WebKit deals with URLs containing a colon character in the host name. That seemingly trivial detail could have potentially led to a cross-site scripting attack.
Apple has patched an issue in how WebKit handles JavaScript that could have led to a buffer overflow condition. The flaw could have led to arbitrary code execution.


